
The insidious Emotet botnet, which staged a go back in November 2021 after a 10-month-long hiatus, is as soon as once more showing indicators of stable enlargement, gathering a swarm of over 100,000 inflamed hosts for perpetrating its malicious actions.
“Whilst Emotet has no longer but attained the similar scale it as soon as had, the botnet is appearing a powerful resurgence with a complete of roughly 130,000 distinctive bots unfold throughout 179 nations since November 2021,” researchers from Lumen’s Black Lotus Labs mentioned in a document.
Emotet, previous to its takedown in past due January 2021 as a part of a coordinated legislation enforcement operation dubbed “Ladybird,” had inflamed no fewer than 1.6 million units globally, performing as a conduit for cybercriminals to put in different varieties of malware, corresponding to banking trojans or ransomware, onto compromised methods.
The malware formally resurfaced in November 2021 the usage of TrickBot as a supply car, with the latter shuttering its assault infrastructure past due closing month after a number of key individuals of the gang have been absorbed into the Conti ransomware cartel.
Emotet’s resurrection is alleged to had been orchestrated by way of the Conti gang itself in an try to shift ways in keeping with higher legislation enforcement scrutiny into the TrickBot’s malware distribution actions.
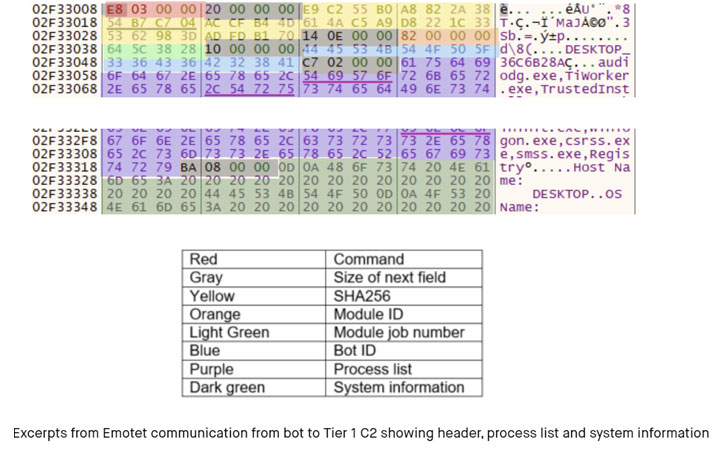
Black Lotus Labs famous that the “aggregation of bots actually did not start in earnest till January [2022],” including the brand new variants of Emotet have swapped the RSA encryption scheme in want of elliptic curve cryptography (ECC) to encrypt community site visitors.
Grasp the Artwork of Darkish Internet Intelligence Amassing
Be told the artwork of extracting risk intelligence from the darkish internet – Sign up for this expert-led webinar!
Some other new addition to its functions is its skill to assemble further machine data past an inventory of operating processes from the compromised machines.
What is extra, Emotet’s botnet infrastructure is alleged to surround just about 200 command-and-control (C2) servers, with many of the domain names positioned within the U.S., Germany, France, Brazil, Thailand, Singapore, Indonesia, Canada, the U.Okay., and India.
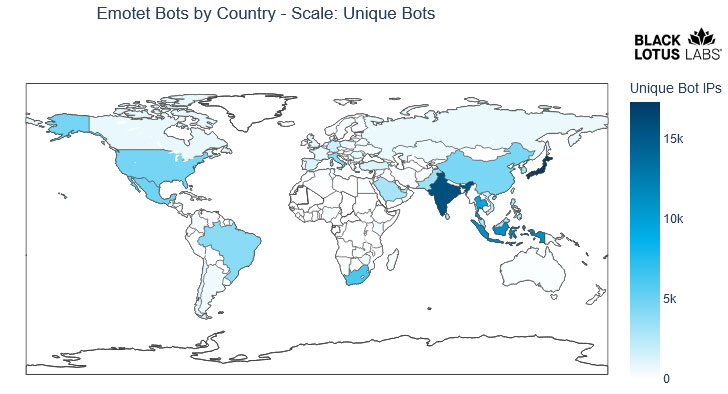
Inflamed bots, alternatively, are closely concentrated in Asia, mainly Japan, India, Indonesia, and Thailand, adopted by way of South Africa, Mexico, the U.S., China, Brazil, and Italy. “This isn’t unexpected given the preponderance of prone or old-fashioned Home windows hosts within the area,” the researchers mentioned.
“The expansion and distribution of bots is a very powerful indicator of Emotet’s development in restoring its as soon as sprawling infrastructure,” Black Lotus Labs famous. “Each and every bot is a possible foothold to a coveted community and items a chance to deploy Cobalt Strike or ultimately be promoted to a Bot C2.”
Supply Through https://thehackernews.com/2022/03/emotet-botnets-latest-resurgence.html


