A risk actor with affiliations to the cyber conflict department of Hamas has been related to an “elaborate marketing campaign” concentrating on high-profile Israeli folks hired in delicate protection, legislation enforcement, and emergency services and products organizations.
“The marketing campaign operators use subtle social engineering tactics, in the end aimed to ship up to now undocumented backdoors for Home windows and Android gadgets,” cybersecurity corporate Cybereason stated in a Wednesday record.
“The objective in the back of the assault used to be to extract delicate knowledge from the sufferers’ gadgets for espionage functions.”
The monthslong intrusions, codenamed “Operation Bearded Barbie,” were attributed to an Arabic-speaking and politically-motivated crew referred to as Arid Viper, which operates out of the Center East and may be identified by way of the monikers APT-C-23 and Desolate tract Falcon.
Maximum lately, the risk actor used to be held liable for assaults geared toward Palestinian activists and entities beginning round October 2021 the use of politically-themed phishing emails and decoy paperwork.
The newest infiltrations are notable for his or her explicit focal point on plundering knowledge from computer systems and cell gadgets belonging to Israeli folks by way of luring them into downloading trojanized messaging apps, granting the actors unfettered get right of entry to.
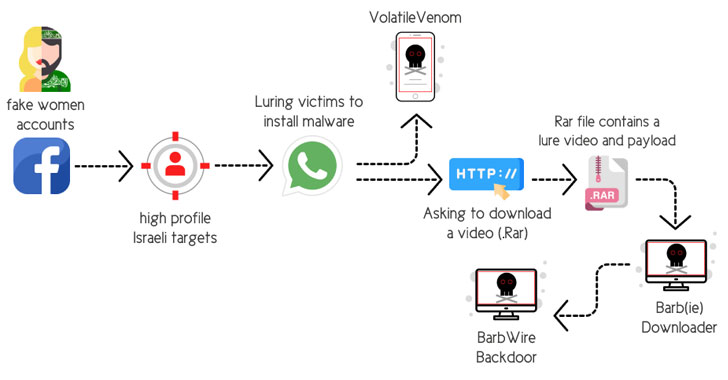
The social engineering assaults concerned the usage of pretend personas on Fb, depending at the tactic of catfishing to arrange fictitious profiles of horny younger ladies to realize the believe of the focused folks and befriend them at the platform.
“After gaining the sufferer’s believe, the operator of the pretend account suggests migrating the dialog from Fb over to WhatsApp,” the researchers elaborated. “Through doing so, the operator temporarily obtains the objective’s cell quantity.”
As soon as the chat shifts from Fb to WhatsApp, the attackers recommend the sufferers that they set up a protected messaging app for Android (dubbed “VolatileVenom”) in addition to open a RAR archive report containing particular sexual content material that results in the deployment of a malware downloader referred to as Barb(ie).
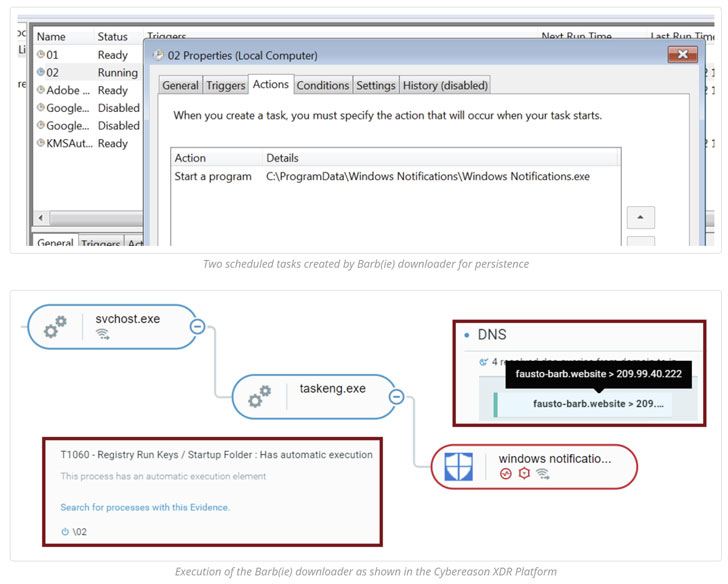
Different hallmarks of the marketing campaign have incorporated the gang leveraging an upgraded arsenal of malware equipment, together with the BarbWire Backdoor, which is put in by way of the downloader module.
The malware serves as a device to fully compromise the sufferer gadget, permitting it to ascertain endurance, harvest saved knowledge, document audio, seize screenshots, and obtain further payloads, all of which is transmitted again to a far off server.
Uncover the Hidden Risks of 3rd-Birthday party SaaS Apps
Do you know of the dangers related to third-party app get right of entry to in your corporate’s SaaS apps? Sign up for our webinar to be told concerning the kinds of permissions being granted and easy methods to decrease chance.
VolatileVenom, then again, is Android adware that is identified to spoof respectable messaging apps and masquerade as device updates and which has been put to make use of in numerous campaigns by way of Arid Viper since a minimum of 2017.
One such instance of a rogue Android app is named “Wink Chat,” the place sufferers making an attempt to enroll to make use of the appliance are introduced an error message that “it is going to be uninstalled,” just for it to stealthily run within the background and extract all kinds of information from the cell gadgets.
“The attackers use a fully new infrastructure this is distinct from the identified infrastructure used to focus on Palestinians and different Arabic-speakers,” the researchers stated.
“This marketing campaign displays a substantial step-up in APT-C-23 features, with upgraded stealth, extra subtle malware, and perfection in their social engineering tactics which contain offensive HUMINT features the use of an excessively lively and well-groomed community of pretend Fb accounts which have been confirmed relatively efficient for the gang.”
Supply Through https://thehackernews.com/2022/04/hamas-linked-hackers-targeting-high.html


