A contemporary Hive ransomware assault performed by means of an associate concerned the exploitation of “ProxyShell” vulnerabilities within the Microsoft Change Server that have been disclosed closing 12 months to encrypt an unnamed buyer’s community.
“The actor controlled to reach its malicious objectives and encrypt the surroundings in not up to 72 hours from the preliminary compromise,” Varonis safety researcher, Nadav Ovadia, stated in a autopsy research of the incident.
Hive, which was once first noticed in June 2021, follows the profitable ransomware-as-a-service (RaaS) scheme followed by means of different cybercriminal teams in recent times, enabling associates to deploy the file-encrypting malware after gaining a foothold into their sufferers’ networks.
ProxyShell — tracked as CVE-2021-31207, CVE-2021-34523, and CVE-2021-34473 — comes to a mix of safety function bypass, privilege escalation, and far off code execution within the Microsoft Change Server, successfully granting the attacker the facility to execute arbitrary code on affected servers.
The problems have been addressed by means of Microsoft as a part of its Patch Tuesday updates for April and Would possibly 2021.
On this case, a success exploitation of the failings allowed the adversary to deploy internet shells at the compromised server, the usage of them to run malicious PowerShell code with SYSTEM privileges to create a brand new backdoor administrator consumer, hijack the area admin account, and carry out lateral motion.
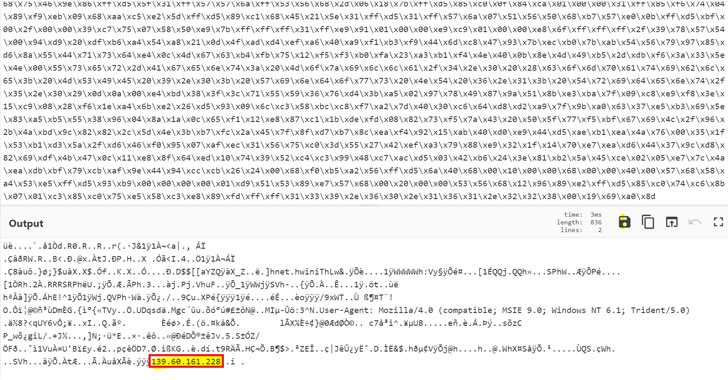
The internet shells used within the assault are stated to had been sourced from a public git repository and given filenames containing a random mixture of characters to evade detection, Ovadia stated. Additionally accomplished was once an extra obfuscated PowerShell script that is a part of the Cobalt Strike framework.
Uncover the Hidden Risks of 3rd-Birthday party SaaS Apps
Have you learnt of the hazards related to third-party app get entry to for your corporate’s SaaS apps? Sign up for our webinar to be told in regards to the forms of permissions being granted and the way to reduce chance.
From there, the risk actor moved to scan the community for treasured information, earlier than continuing to deploy the Golang ransomware executable (named “Home windows.exe”) to finish the encryption procedure and show the ransom word to the sufferer.
Different operations performed by means of the malware come with deleting shadow copies, turning off safety merchandise, and clearing Home windows tournament logs to keep away from detection, save you restoration, and make sure that the encryption occurs with none hiccup.
If the rest, the findings are but any other indicator that patching for recognized vulnerabilities is essential to thwarting cyberattacks and different nefarious actions.
“Ransomware assaults have grown considerably over the last years and stay the most well liked manner of risk actors aiming to maximise income,” Ovadia stated. “It is going to doubtlessly hurt a company’s recognition, disrupt common operations and result in brief, and most likely everlasting, lack of delicate information.”
Supply By way of https://thehackernews.com/2022/04/new-incident-report-reveals-how-hive.html


