
An unbiased safety researcher has shared what is an in depth timeline of occasions that transpired because the infamous LAPSUS$ extortion gang broke right into a third-party supplier connected to the cyber incident at Okta in past due January 2022.
In a suite of screenshots posted on Twitter, Invoice Demirkapi printed a two-page “intrusion timeline” allegedly ready via Mandiant, the cybersecurity company employed via Sitel to analyze the protection breach. Sitel, thru its acquisition of Sykes Enterprises in September 2021, is the third-party carrier supplier that gives buyer improve on behalf of Okta.
The authentication products and services supplier printed final week that on January 20, it used to be alerted to a brand new issue that used to be added to a Sitel buyer improve engineer’s Okta account, an try that it mentioned used to be a success and blocked.
The incident most effective got here to mild two months later after LAPSUS$ posted screenshots on their Telegram channel as proof of the breach on March 22.
The malicious actions, which gave the danger actor get admission to to almost 366 Okta consumers, happened over a five-day window between January 16 and 21, all through which the hackers performed other stages of the assault, together with privilege escalation after gaining an preliminary foothold, keeping up endurance, lateral motion, and interior reconnaissance of the community.
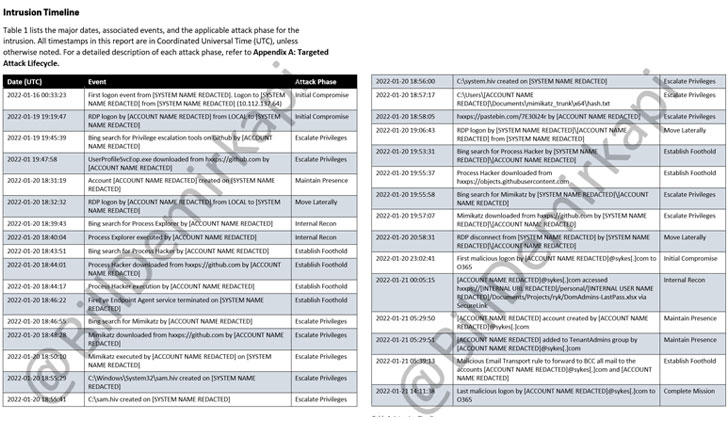
Okta claimed that it had shared signs of compromise with Sitel on January 21 and that it gained a abstract record in regards to the incident from Sitel most effective on March 17. Therefore, on March 22, the similar day the prison crew shared the screenshots, it mentioned it received a duplicate of your entire investigation record.
Therefore, on March 22, the similar day the prison crew shared the screenshots, it received a duplicate of your entire investigation record.
“Even if Okta gained the Mandiant record in March explicitly detailing the assault, they endured to forget about the most obvious indicators that their atmosphere used to be breached till LAPSUS$ shined a focus on their inactiveness,” Demirkapi wrote in a tweet thread.
Grow to be an Incident Reaction Professional!
Liberate the secrets and techniques to bulletproof incident reaction – Grasp the 6-Segment procedure with Asaf Perlman, Cynet’s IR Chief!
The San Francisco-based corporate, in an in depth FAQ posted on March 25, said that its failure to inform its customers in regards to the breach in January used to be a “mistake.”
“In mild of the proof that we have got accrued within the final week, it’s transparent that we might have made a distinct choice if we were in ownership of the entire info that we have got lately,” Okta mentioned, including it “must have extra actively and forcefully pressured data from Sitel.”
Sitel, for its phase, mentioned it is “cooperating with regulation enforcement” at the incident and has clarified that the breach affected “a portion of the legacy Sykes community most effective,” including it “took swift motion to include the assault and to inform and give protection to any doubtlessly impacted shoppers who have been serviced via the legacy group.”
The improvement comes because the Town of London Police informed The Hacker Information final week that seven other folks hooked up to the LAPSUS$ gang have been arrested and therefore launched underneath investigation. “Our enquiries stay ongoing,” the company added.
Supply Through https://thehackernews.com/2022/03/new-report-on-okta-hack-reveals-entire.html


