
Two weeks after main points emerged a couple of 2d records wiper pressure delivered in assaults in opposition to Ukraine, but one other harmful malware has been detected amid Russia’s proceeding army invasion of the rustic.
Slovak cybersecurity corporate ESET dubbed the 3rd wiper “CaddyWiper,” which it stated it first noticed on March 14 round 9:38 a.m. UTC. Metadata related to the executable (“caddy.exe“) presentations that the malware used to be compiled at 7:19 a.m. UTC, a bit over two hours previous to its deployment.
CaddyWiper is notable for the truth that it does not proportion any similarities with up to now found out wipers in Ukraine, together with HermeticWiper (aka FoxBlade or KillDisk) and IsaacWiper (aka Lasainraw), the 2 of that have been deployed in programs belonging to govt and industrial entities.
“Without equal objective of the attackers is the identical as with IsaacWiper and HermeticWiper: make the programs unusable by means of erasing person records and partition knowledge,” Jean-Ian Boutin¸ head of risk analysis at ESET, advised The Hacker Information. “All the organizations centered by means of the hot wiper assaults had been both within the governmental or monetary sector.”
Not like CaddyWiper, each the HermeticWiper and IsaacWiper malware households are stated to had been in construction for months upfront prior to their free up, with oldest identified samples compiled on December 28 and October 19, 2021, respectively.
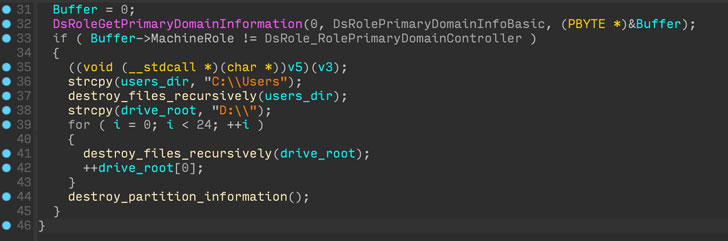
However the newly found out wiper stocks one tactical overlap with HermeticWiper in that the malware, in a single example, used to be deployed by means of the Home windows area controller, indicating that the attackers had taken regulate of the Energetic Listing server.
“Apparently, CaddyWiper avoids destroying records on area controllers,” the corporate stated. “That is most probably some way for the attackers to stay their get admission to within the group whilst nonetheless anxious operations.”
The wiper is programmed to systematically break all recordsdata situated in “C:Customers,” prior to transferring directly to the following force letter and erasing the recordsdata till it reaches the “Z” force, that means CaddyWiper will even try to wipe any community mapped force hooked up to the machine.
Grasp the Artwork of Darkish Internet Intelligence Collecting
Be told the artwork of extracting risk intelligence from the darkish internet – Sign up for this expert-led webinar!
“The document destruction set of rules consists of 2 levels: a primary degree to overwrite recordsdata and one other to break the bodily disk format and the partition tables along side it,” Cisco Talos researchers stated in an research of the malware. “Destroying the beginning of the recordsdata and the walls tables is a not unusual method observed on different wipers, and its extremely efficient in fighting document restoration.”
Microsoft, which has attributed the HermeticWiper assaults to a risk cluster tracked as DEV-0665, stated the “supposed purpose of those assaults is the disruption, degradation, and destruction of centered sources” within the nation.
The advance additionally arrives as cybercriminals have opportunistically and an increasing number of capitalized at the warfare to design phishing lures, together with topics of humanitarian help and more than a few varieties of fundraising, to ship plenty of backdoors corresponding to Remcos.
“The worldwide passion within the ongoing battle in Ukraine makes it a handy and efficient information match for cybercriminals to take advantage of,” Cisco Talos researchers stated. “If a undeniable subject of trap goes to extend the possibilities of a possible sufferer putting in their payload, they are going to use it.”
However it is not simply Ukraine that is been on the receiving finish of wiper assaults. Closing week, cybersecurity company Pattern Micro disclosed main points of a .NET-based wiper referred to as RURansom that has solely centered entities in Russia by means of encrypting the recordsdata with a randomly generated cryptographic key.
“The keys are distinctive for every encrypted document and don’t seem to be saved anyplace, making the encryption irreversible and staining the malware as a wiper slightly than a ransomware variant,” the researchers famous.
Supply Through https://thehackernews.com/2022/03/caddywiper-yet-another-data-wiping.html


